
Key Takeaways:
- A massive npm packages hack inserted crypto-stealing malware into 18 common, widely used libraries.
- The malware hijacks browser functions to silently alter crypto transaction destinations without you even noticing.
- Two leading hardware wallet providers, like Ledger and Trezor, have confirmed their systems were unaffected.
Table of Contents
The Analysis of the NPM Packages Hack
In one of the largest software supply chain attacks to date, hackers injected sophisticated malware built specifically to steal crypto into 18 popular Node Package Manager (NPM) packages, namely ‘chalk‘ and ‘debug‘. The npm packages hack impacted tools that had over two billion downloads a week combined, putting millions of Web3 developers and users at risk.
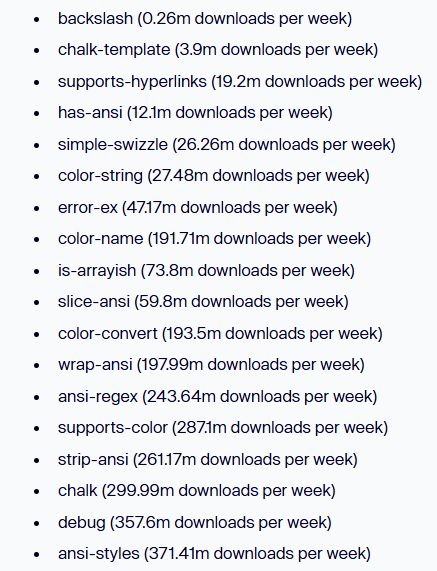
The security breach started when a maintainer of those important open-source libraries was tricked by a sophisticated phishing email.

Then:
- The attacker, pretending to be NPM support from a typosquatted domain (npmjs.help), convinced the user to provide his credentials.
- Once the attacker had access, he published malicious updates to the packages.
- The updates included obfuscated code that functions as “clipper” malware once executed in a browser.
- The malware attaches itself in a way that allows it to listen to important web functions like fetch, XMLHttpRequest, and Web3 wallet interfaces, to hover for cryptocurrency addresses only meant to be viewed when the user is to sign the transaction and swap them for the attacker’s instead.
A Narrowly Averted Catastrophe
To this point, while the potential harm was significant, the developer, John Junon, acted quickly to minimize the damage from the attack. After being informed of malicious packages, he began removing them quickly before NPM suspended his account to contain the breach.
Aikido Security, which investigated the incident, stated they tracked “about $970” stolen, which is remarkably low given the magnitude of the potential exposure due to the developer’s quick action.
Read also: Fake AI Startups Drain Crypto Wallets in Sophisticated Social Engineering Scam
Industry Response and Assurance
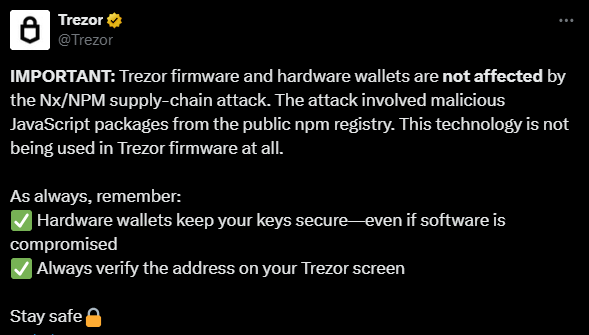
The crypto community responded quickly. Ledger and Trezor, two of the leading hardware wallet manufacturers, both issued statements assuring users that their devices and companion software were not compromised because their security models protect against these types of client-side attacks.
This incident has triggered renewed discussion in the open-source software supply chain community about vulnerabilities, along with the need for better security protocols for maintainers.
A Sobering Wake-Up Call
The npm packages hack serves as a stark reminder that the security of the entire digital ecosystem often rests on individual maintainers. It demonstrates a profound flaw in the open-source model and emphasizes the necessity for developers to take a “trust but verify” attitude to these processes. This may mean potentially using internal repositories in order to vet public packages before using them.
Final Thought: Will this incident cause a fundamental rethinking of how we secure the open-source software supply chain that powers modern tech, and especially crypto, as attacks become more sophisticated?
FAQs
What is a supply chain attack?
It’s when hackers compromise a software component that others depend on, infecting all downstream users.
How does the “clipper” malware work?
It secretly runs in your browser, watching for crypto addresses and swapping them with the hacker’s address before you confirm a transaction.
Was my Ledger/Trezor wallet safe?
Yes. Both companies confirmed their hardware and software were not vulnerable to this specific attack.
For more cybercrime stories, read: Cybercrime Alarm: GreedyBear Hackers Steal $1M Via Weaponized Firefox Extensions


