
Key Takeaways:
- 650+ cybercrime attack tools used: 150+ infected Firefox extensions, 500+ malware executables, fake crypto sites.
- $1M stolen via “extension hollowing”: Legitimate add-ons turned malicious after marketplace approval.
- Centralized infrastructure: All attacks routed through a single Russian IP address (185.208.156.66).
- AI-generated code enables fast scaling and evasion of security tools.
Table of Contents
The Heist: Industrial-Scale Crypto Theft
Imagine a cybercrime organization working as efficiently as a Fortune 500 company. That might just be a description of GreedyBear, a Russian hacking organization responsible for stealing over a million dollars’ worth of crypto, utilizing trust in the tools that everyday users rely on. According to Koi Security, GreedyBear’s campaign works with 150+ malicious Firefox extensions, almost 500 malware executables, and dozens of phishing sites.
This is a wake-up call for any crypto user; even browser add-ons aren’t safe anymore.
How GreedyBear Operates: The 3-Pronged Attack
1. The Firefox Extension Trap
GreedyBear’s most devastating vector targets MetaMask, Exodus, and TronLink users. The cybercrime group creates and uploads harmless extensions at first (e.g., YouTube downloaders) to the Firefox marketplace (let’s say a generic extension directory on Web3), then floods them with fake reviews. Once the extension is approved, they basically “hollow out” the code, filling it with malicious logic that can steal wallet credentials when users type them.
- “They bypass security by building trust first, then injecting poison,” explains Koi Security researcher Tuval Admoni.
2. Malware for the Masses
Almost 500 hacked .exe files, the majority credential stealers such as LummaStealer and ransomware variants, were distributed through Russian piracy sites (for example, rsload.net). Victims downloading “cracked” software unwittingly installed trojans siphoning cryptocurrency.
3. Slick Scam Websites
Fake landing pages for “hardware wallets” (i.e., jupiterwallet.co.com.trezor-wallet.io) and “wallet repair services” (secure-wallets.co.com) collect user credentials and credit cards. These sites take it a step further than a basic phishing site, as they contain a more legitimate appearance and resemble businesses still operating.
The AI-Powered Threat Factory
GreedyBear’s operations are frighteningly effective:
- One server to rule them all: Every single attack routes back to 185.208.156.66 in Russia.
- AI-assisted code generation: Allowed extremely rapid creation of different malware variants to remain undetected by signature-based detection.
- Global reach: It is mainly targeting Russian speakers via malware, but targeting English-speaking users via extensions.
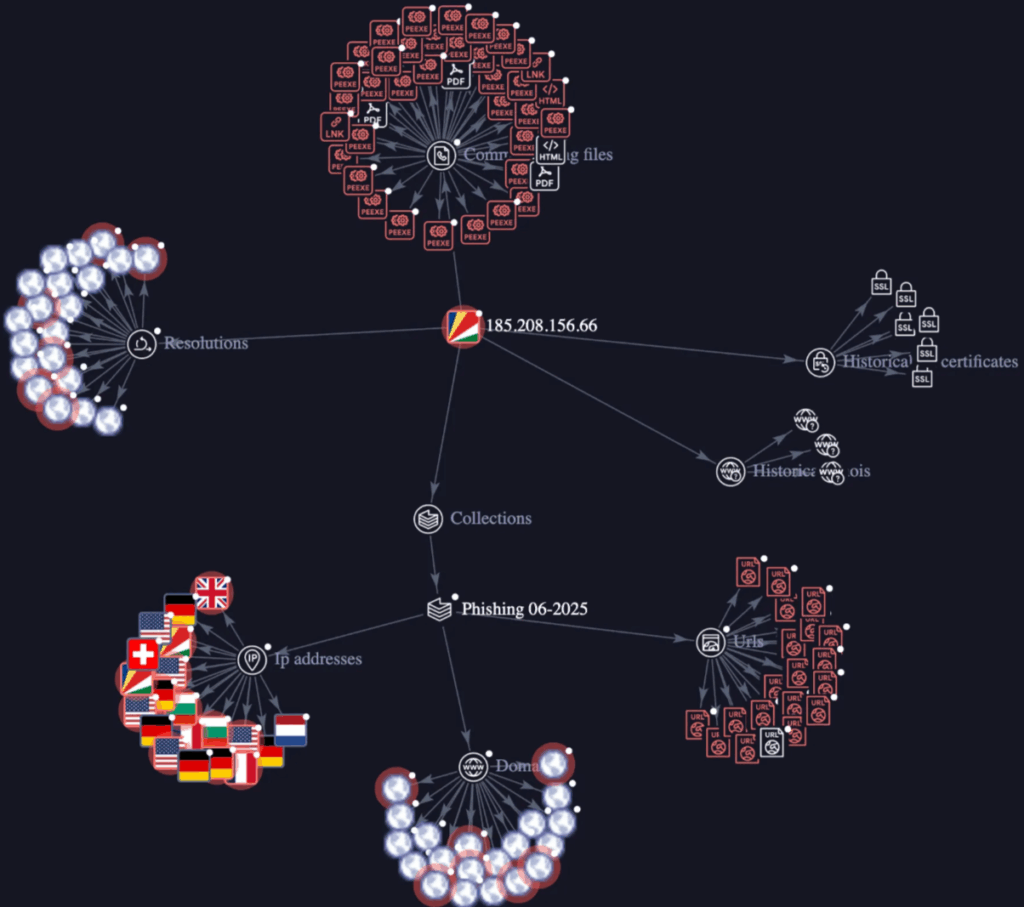
So far, the cybercrime group knows very well how to exploit trust in browser extension stores. The legacy security is not able to stop it.
How to Protect Your Crypto
- Stay away from third-party extensions: Make sure to only download wallets from the official developers’ websites.
- Forget about using browsers – use hardware: Use Ledger or Trezor wallets (buy from their actual manufacturer sites).
- Do not download cracked software: Pirated software is a pathway to malware.
- Check and double-check domains: Scammers will change domains slightly (e.g., trezor-wallet.io instead of trezor.io).
The New Normal in Crypto Crime
Of course, GreedyBear is not a lone wolf; it’s one of many active hacking groups. AI is here to help us, but its negative side democratizes cybercrime, expecting to be increasingly bold, intelligent, and untraceable. For the crypto community, vigilance is a must. Browser extensions? Just assume they’re unsafe. Too-good-to-be-true downloads? They might be traps.
Final Thought: Your crypto wallet’s security now depends less on code and more on distrust. How will you adapt?
For more crypto cybercrime stories, read: Shocking LuBian Bitcoin Hack: How $3.5B Vanished in Crypto’s Biggest Heist


