
Key Takeaways:
- Venus Protocol recovered $13.5M stolen as part of a phishing attack.
- The protocol temporarily disabled itself and passed an emergency governance vote, which allowed for the liquidation of assets in the attacker’s positions.
- This incident highlights ongoing social engineering risks in decentralized finance (DeFi) despite secure smart contracts.
Table of Contents
The Phishing Scam Attack
In an incredible turn of events, Venus Protocol has successfully recovered 13.5 million of user assets that were stolen during a sophisticated phishing attack. It all started when a high-value user (known in crypto circles as a “whale”) accidentally approved a malicious contract that allowed the perpetrator access to their account. The hacker then immediately withdrew the wrapped Bitcoin (BTCB), some stablecoins, and other assets from that account.
While Venus Protocol demonstrates the reasonable actions for crisis management, it also shows that, despite the sophisticated nature of smart contracts, social engineering and legacy risk in decentralized finance (DeFi) are just around the corner.
A Remarkable Response
This was not a protocol-level exploit targeting a smart contract vulnerability, but rather a “social engineering” scheme where the user was tricked into approving an unauthorized transaction. The Venus Protocol team was able to enact an emergency pause mechanism, freezing all operations on the platform, just hours after the exploit was discovered, which stopped the attacker from moving the stolen assets off-chain or closing positions.
The Community Power
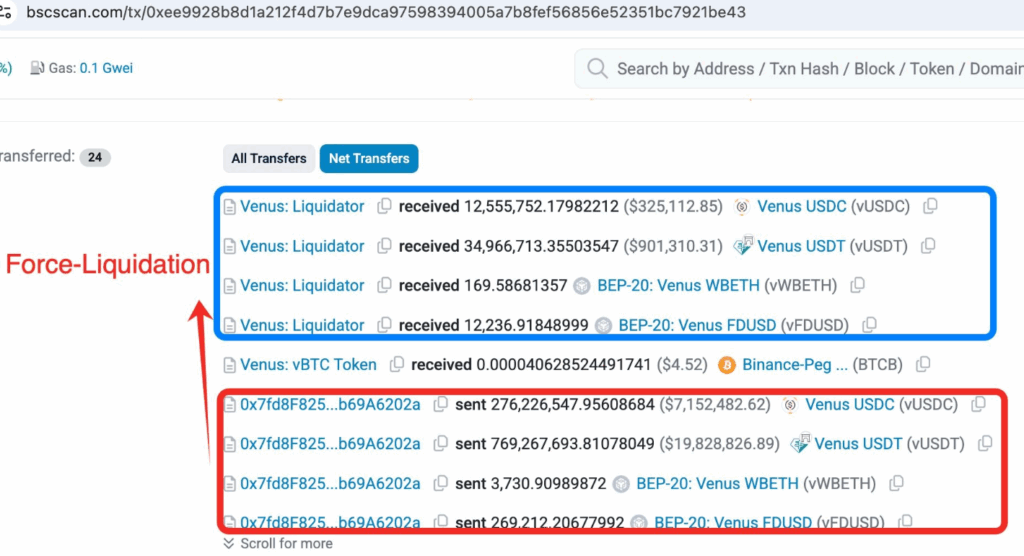
The true recovery operation was initiated when a Venus Protocol emergency governance vote was conducted. Venus token holders had a proposal approved within minutes that effectively forced the exploiter’s position, “liquidating” within the protocol itself, while the community was able to recover the stolen funds before the scammer could launder the asset using mixing services or a cross-chain bridge.
After the proposal was approved, the platform’s native token, XVS, dropped nearly 10%; however, the market was able to stabilize once the recovery was confirmed.

A Fresh Decentralization Debate Sparks in the DeFi Space
Celebrating the successful recovery of funds, this incident has ignited renewed debate over decentralization purism versus pragmatic security in the DeFi space.
The emergency measures employed included some centralized intervention points (a protocol pause function and a governance-managed liquidation), and it is at least conceivable that these centralized responses can still be classified as “decentralized.”
However, this raises the larger question of whether or not effective security responses can also remain “decentralized.”
Final Thought: This recovery establishes a new standard for responding to DeFi crises, but it also reminds us about the fact that the most significant vulnerability in blockchain security continues to be the human element.
FAQs
Was this a hack of Venus Protocol?
No, the protocol’s smart contracts remained secure. This was a sophisticated phishing attack that tricked a DeFi user into approving a malicious transaction.
How were the funds recovered?
The Venus protocol was paused, then a governance vote approved forced liquidation of the attacker’s positions within the platform itself.
What’s the difference between hacking and phishing?
Hacking exploits technical vulnerabilities in code. On the other hand, phishing uses social engineering to trick users into revealing credentials or approving malicious transactions.
For more shocking crypto crime stories, read: Social Engineering Attack Drains 783 Bitcoin, Exposes Rising User Vulnerabilities


