
Consensus is the method that makes it possible for a blockchain to operate without the need for a centralized entity. In a decentralized network where participants do not trust one another, consensus protocols define the way transactions are verified, the way the ledger changes are made, and how the network is kept safe from the attackers. Proof of work and proof of stake are the two leading methods used to address this issue. These consensus methods are distinct in the assumptions about economics, security models, and a set of trade-offs.
What consensus means in blockchain networks
Consensus is fundamentally a mutual agreement. In the context of blockchains, it means a common understanding among a distributed network in terms of transaction validity as well as the order in which they took place. Every node has a copy of the ledger. For the mechanism to work, all honest nodes must agree on the truth, even if cheating is attempted. The Byzantine Generals Problem addressed this issue long before blockchains emerged. It depicts a scenario where the entities involved have to coordinate without trusting each other and, at the same time, assume that some of the actors may be malicious.
Blockchains ensure that participants operate honestly by demanding that validators stake something of economic value that is scarce. If the validators perform correctly, they are given rewards in accordance with the protocol, while if they deviate, they suffer a direct financial loss. Proof of Work and Proof of Stake are significantly different in how they approach the challenge.
Proof of Work (PoW) explained
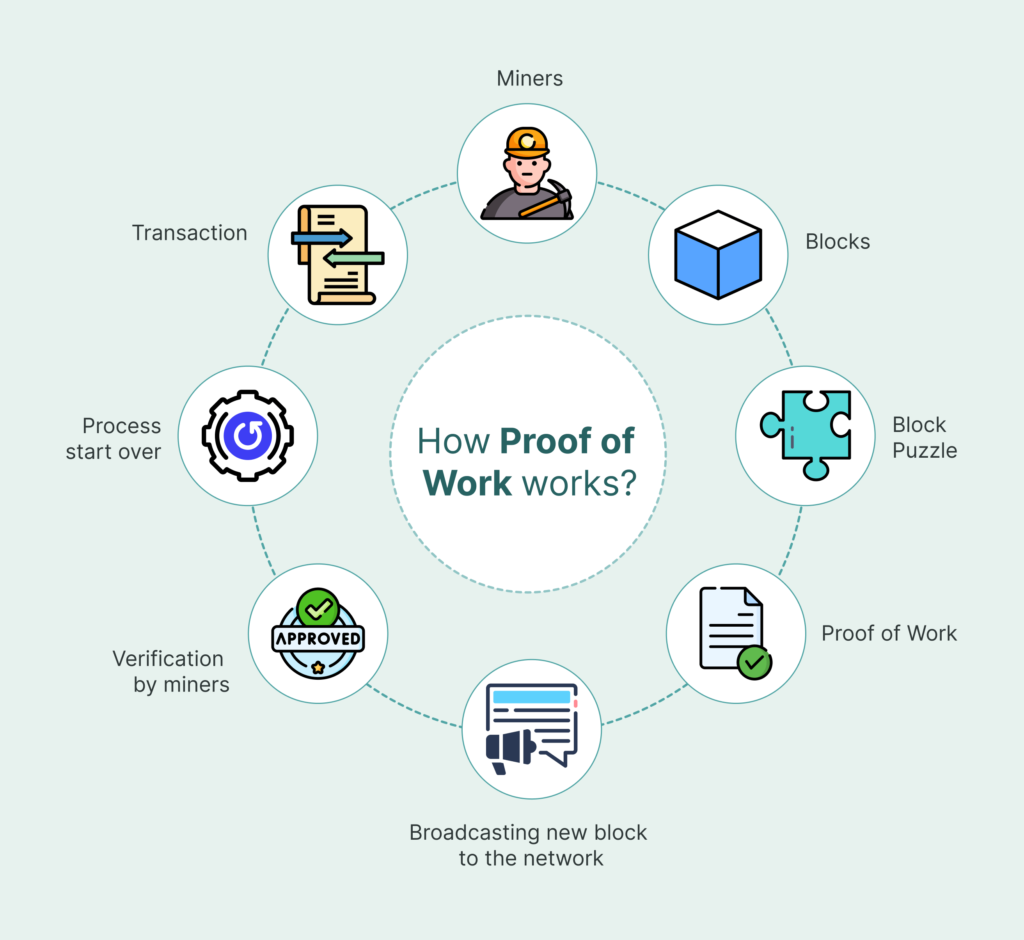
To secure a blockchain, the proof of work requires participants, known as miners, to perform a computational task. The task is expensive, verifiable, and difficult to counterfeit. Proof of work was first conceptualized from the work on limiting email spam. While sending one message was easy, sending millions became prohibitively expensive because of the computation required. Bitcoin subsequently employed this concept to protect its decentralized ledger. Consequently, miners in the Bitcoin network continuously input transaction data to a cryptographic hashing function. After a hashing attempt, a random output is generated and miners continue the process until they achieve a hash that meets the difficulty criteria of the respective network.
The miner is granted the right to add a new block of transactions after determining a valid hash. The other nodes independently verify the block. In the case of a valid block, it is recorded on the blockchain, and the miner is granted the reward. In the instance of an invalidation of the block, the work is discarded, and the effort is wasted.
Examples of Proof-of-Work blockchains
- Bitcoin
- Litecoin
- Monero
- Dogecoin
- Ethereum Classic
Mining rewards and network security
Miners receive newly issued bitcoins as well as transaction fees. Bitcoin operates on a fixed monetary schedule in which block rewards are lowered approximately every four years by a mechanism called the Bitcoin halving. To minimize volatility, many miners participate through mining pools, where they share computational power and rewards. Security comes from verification and every block must be checked by the network before it is finalized. To manipulate the chain, an attacker would need control over more than half of the total computational power. As networks grow, this procedure becomes costly and impractical.
Block creation occurs at predefined intervals. Bitcoin produces a new block roughly every ten minutes, while other networks operate on shorter timeframes.
Advantages and limitations of Proof of Work
Proof of Work runs on a secure decentralized system and it is compatible with large-scale public blockchains. To manipulate the network, the attackers need to spend enormous amounts of resources and use powerful hardware with continued energy flow. The energy consumption has been raised as the main criticism against this consensus method. The energy consumption is the factor that makes it difficult for attackers to profit from the network, as their efforts become economically unviable. Also, quite a few mining operations are looking for cheap and renewable energy sources to keep their businesses profitable.
Proof of Stake (PoS) explained
Proof of stake cuts down the energy-consuming race that is a computational competition with an economic commitment. Therefore, instead of consuming electricity, the users of the network have to lock up the network’s native tokens to keep the blockchain secure. These users, known as validators, are the ones who are allowed to issue and confirm blocks on the basis of such things as the value staked and some random selection criteria. This nature serves as a means of minimizing the predictability and the possibility of giving some unfair advantages. Proof of Stake was first introduced in 2012 with the idea of eventually coming up with an energy-saving version of Proof of Work.
Examples of Proof of Stake blockchains
- Ethereum
- Polkadot
- Cardano
- Solana
- Avalanche
- Cosmos
Staking rewards and penalties
Validators receive rewards for the examination and approval of transactions in a correct manner. The users who fail to fulfill the technical or financial conditions may delegate their tokens to staking pools and receive a certain proportion of the rewards. Most proof-of-stake networks utilize slashing to prevent illicit activity. If a validator violates the rules, they may forfeit some of their staked tokens. As a result, any misconduct directly exposes the network to a financial risk. A proof-of-stake validator typically requires significantly less hardware when compared to a proof-of-work mining method.
Validation and trade-offs in Proof of Stake
Proof-of-stake networks continue to rely on independent verification before the blockchain blocks are finalized. Token issuance follows a transparent set of rules defined by each protocol. The main advantage of proof of stake is efficiency. Delegation has the power to greatly lower the amount of energy consumed and make the process more accessible to a larger number of people. The main drawback of this type of consensus is that the risk of stake or resource concentration increases, which in turn affects the degree of decentralization in the network. To put it another way, selecting validators with larger stakes could result in a small group of people controlling most of the power. Staked assets are often locked for a period of time and cannot be freely traded.


