
Key Takeaways
- A WhatsApp 0-click vulnerability exploited via a malicious DNG file grants attackers full device control.
- The attack combines two flaws: a message spoofing bug (CVE-2025-55177) and a DNG parsing flaw (CVE-2025-43300).
- Crypto users are prime targets for this silent spyware, risking private key and wallet drain.
Table of Contents
The Silent Attack Explained
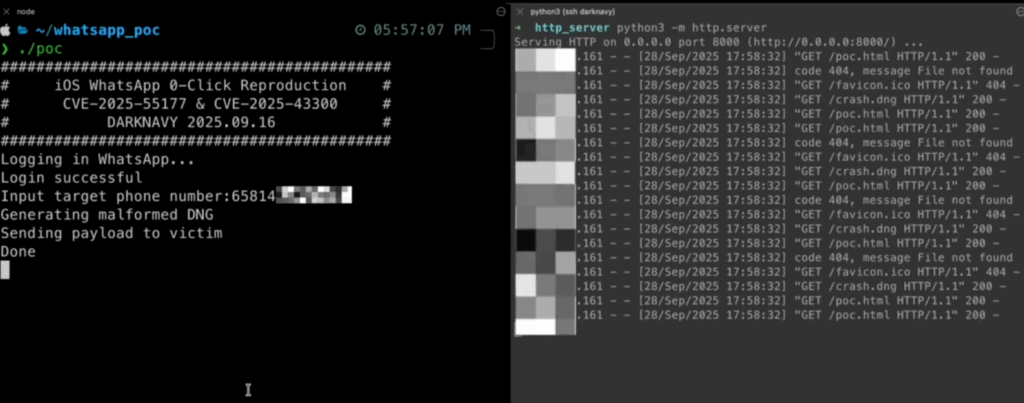
Security researchers have exposed a dangerous WhatsApp 0-click vulnerability exploited to hijack iPhones, Macs, and iPads. A threat actor initiates the attack by sending a specially crafted DNG image file with no user action required; even receiving it compromises the target. This WhatsApp 0-click vulnerability exploited a critical logic flaw in validating messages in WhatsApp, allowing attackers to effectively spoof messages as coming from a trusted mobile device linked to the WhatsApp account.
How The Exploit Chain Unfolds
This breach occurs in a two-step process:
- First vulnerability CVE-2025-55177: The spoofed message bypasses all normal security checks.
- Second vulnerability CVE-2025-43300: The malicious DNG file exploits a memory corruption bug when WhatsApp tries to process it. WhatsApp automatically parses files and automatically executes code, requiring no victim interaction.
Different from attacks that require a click, this WhatsApp 0-click vulnerability exploited the app’s automated file parsing, letting it be completely silent and undetected to the victim. Once successfully breached, the attacker gets full access to the device, all messages, all apps, including crypto wallets, and all stored data.
Read also: Cybercrime Alarm: GreedyBear Hackers Steal $1M Via Weaponized Firefox Extensions
Critical Implications for the Crypto Community
For anyone involved in crypto, this is particularly dangerous. If a device is compromised, someone can steal seed phrases, private keys, and access to exchange apps. The demonstrated WhatsApp 0-click vulnerability exploited suggests that even non-technical targets can easily become victimized with spyware designed to drain digital assets. High-net-worth individuals and project leaders in the industry are probably at the top of a target list for espionage.
Read also: Malaysian MPs Targeted in Coordinated AI Deepfake Extortion for Crypto
Summing Up
This incident serves as a stiff reminder that even the most trusted communication apps can become the weakest link in our digital security without even having any type of interaction. Malicious actors are always working on developing new and more technical attacks that can cause considerable headaches, or worse.
Final Thought: The silent nature of this attack means vigilance and proactive security are non-negotiable nowadays. Updating your applications is the first, primary step to safety.
FAQs
What is a 0-click vulnerability?
It’s a remote code execution (RCE) security vulnerability that allows the exploitation of a device when the victim does not click on anything or take any action.
What is a DNG file?
DNG or Digital Negative refers to a file format for raw images from digital cameras, which, in this case, was maliciously crafted to hack the device.
How can I protect myself?
Immediately update WhatsApp and your device’s operating system to the latest version to patch the vulnerability.
For security breach stories, read: Hyperdrive Smart Contract Exploit Drained of $782,000 in Funds


