
Key Takeaways
- DarkComet RAT hidden in fake Bitcoin tool exposes users to complete system compromise.
- Malware uses Ultimate Packer for Executables (UPX) packing and registry manipulation for stealth persistence.
- Attack captures keystrokes and establishes remote control over infected devices.
Table of Contents
Sophisticated Malware Campaign Exploits Crypto Interest
According to security researchers, they have identified a dangerous new campaign that distributes DarkComet RAT hidden in fake Bitcoin tool applications, targeting crypto enthusiasts seeking wallet software.
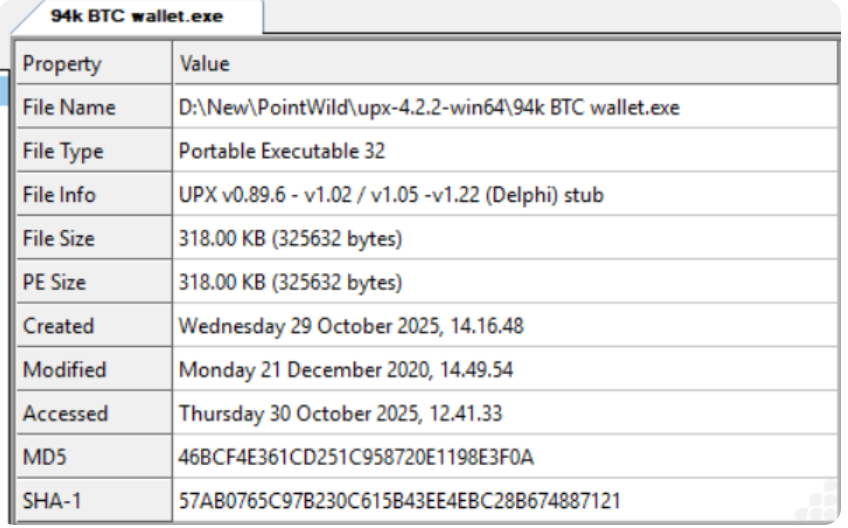
This malware arrives compressed in a Roshal Archive (RAR) containing an executable file named “94k BTC wallet.exe” that unpacks the notorious Remote Access Trojan (RAT) instead of legitimate Bitcoin functionality.
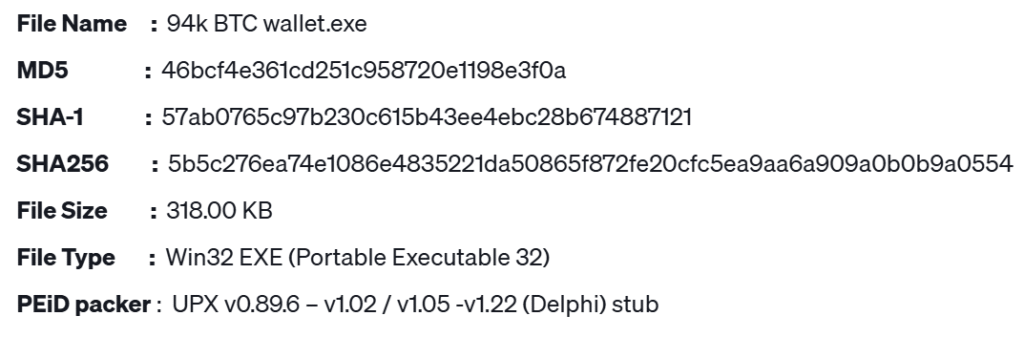
This DarkComet RAT hidden in fake Bitcoin tool shows how cybercriminals are continuously repurposing old malware to combine with new social engineering lures to compromise unsuspecting victims.
Read also: Cybercrime Alarm: GreedyBear Hackers Steal $1M Via Weaponized Firefox Extensions
Technical Sophistication and Stealth Mechanisms
The DarkComet RAT hidden in fake Bitcoin tool uses several evasion techniques, including Ultimate Packer for Executables (UPX) compression to avoid detection and complex persistence techniques. To this point, once executed, the malware copies itself to the AppData folder as “explorer.exe” and creates multiple malicious registry run keys to ensure automatic startup with every system reboot.
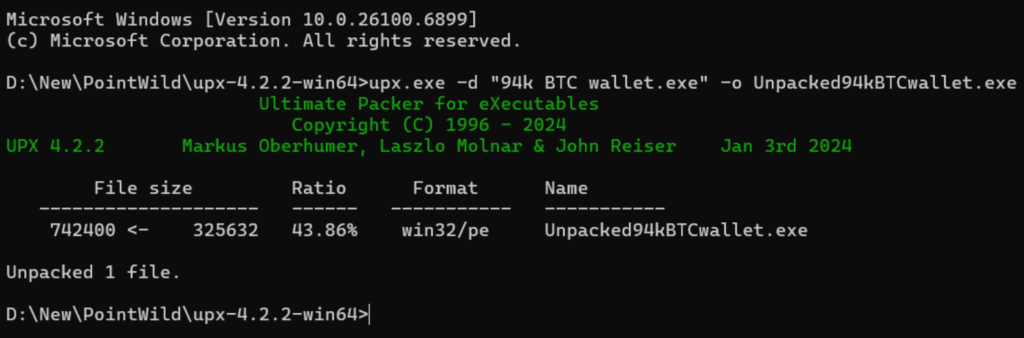
Then, the DarkComet RAT hidden in fake Bitcoin tool establishes a connection with command-and-control server kvejo991.ddns.net on port 1604, allowing attackers to remotely control infected systems, capture keystrokes, and potentially steal crypto wallet credentials and ultimately, your funds.
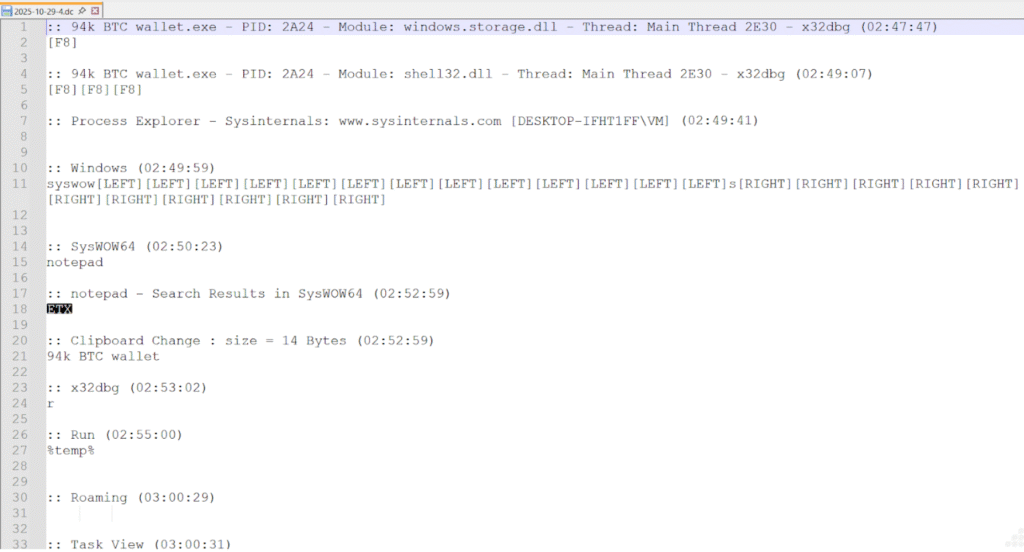
Read also: CZ Targeted by Government-Backed Hackers, Suspects North Korean Lazarus Group
Critical Protection Measures
Users can protect themselves from threats like the DarkComet RAT hidden in fake Bitcoin tool by following these essential security practices:
- Make sure to download crypto software only from official, verified sources
- Always avoid opening compressed archives from unknown senders
- Regularly monitor system registry and running processes for anomalies
- Verify file hashes before executing any financial-related software
- Use comprehensive antivirus solutions with enhanced behavioral detection
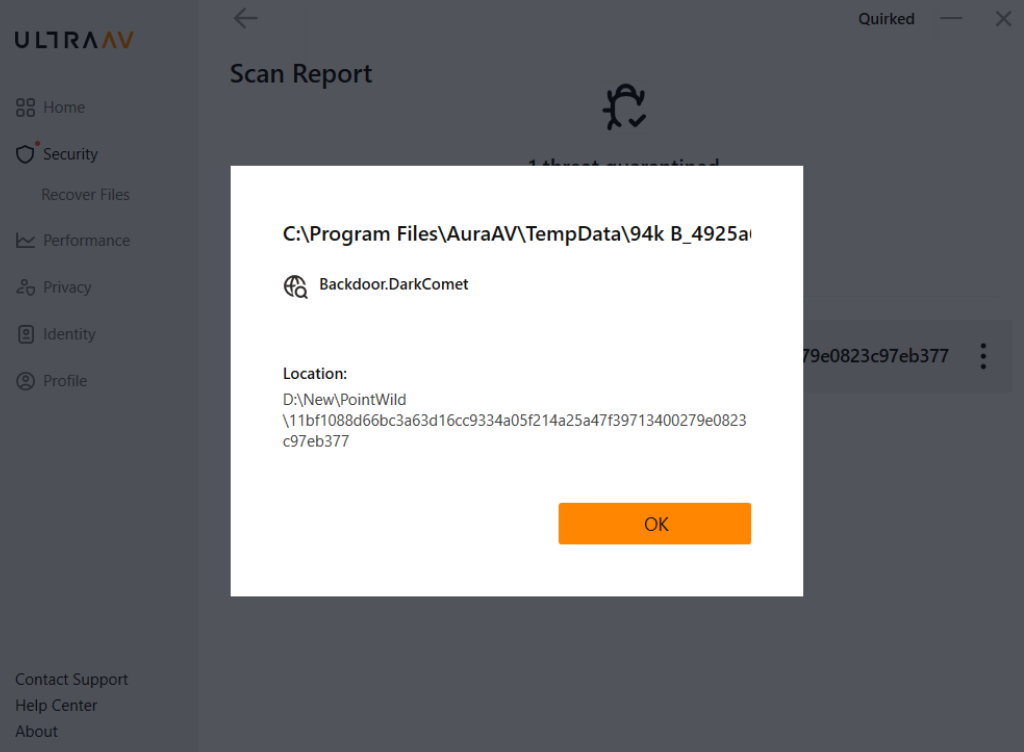
Read also: The TimesCrypto Crime Report: Unmasking the New Wave of Sophisticated Crypto Scams
Constant Vigilance Required in Crypto Space
The revival of the DarkComet RAT hidden in fake Bitcoin tool is an obvious reminder of the constant threats that crypto users experience. Although the creator of the DarkComet RAT ceased development several years ago, the malware remains tremendously potent in the hands of cybercriminals who combine it with compelling crypto lures.
This incident sets a clear and strong reminder that being security-aware is just as important as being buffered with technology in the digital assets ecosystem.
FAQs
What is the DarkComet RAT hidden in fake Bitcoin tool?
The DarkComet RAT hidden in fake Bitcoin tool is a remote access trojan disguised as crypto wallet software that gives attackers complete control over infected systems, enabling keystroke logging, file theft, and surveillance.
How does the DarkComet RAT hidden in fake Bitcoin tool infect systems?
The DarkComet RAT hidden in fake Bitcoin tool typically arrives in compressed RAR archives that users must manually extract and execute, often distributed through phishing emails, malicious websites, or file-sharing platforms.
What should I do if I encounter the DarkComet RAT hidden in fake Bitcoin tool?
If you suspect infection by the DarkComet RAT hidden in fake Bitcoin tool or any other software, immediately disconnect from the internet, run antivirus scans, check for suspicious registry entries, and consider reinstalling your operating system to ensure complete removal.
For more crypto malware-related stories, read: Crypto-Stealing Malware Found in 18 Popular NPM Packages


