
Key Takeaways
- GANA Payment Exploit results in over $3.1 million stolen from BSC project.
- Attacker laundered 1,140 BNB ($1.04M) through Tornado Cash before bridging to Ethereum.
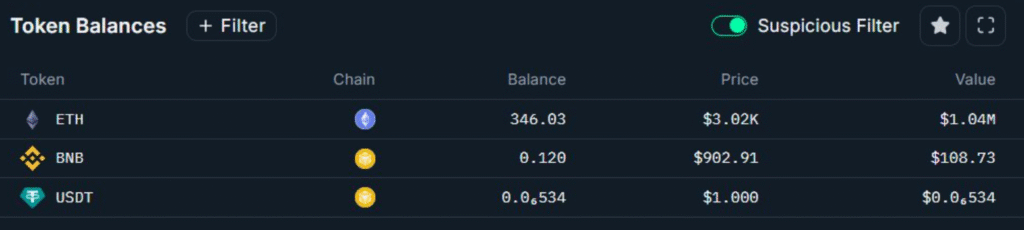
- 346 ETH ($1.046M) remains dormant in attacker’s Ethereum wallet awaiting movement.
Table of Contents
Sophisticated Attack Targets Payment Infrastructure Project
According to blockchain investigator ZachXBT, who first reported on the security incident, the GANA Payment Exploit has resulted in a catastrophic loss of $3.1 million. The exploit centered on GANA Payment’s deployment on Binance Smart Chain, wherein an unidentified attacker methodically drained GANA’s funds before executing money laundering methods.
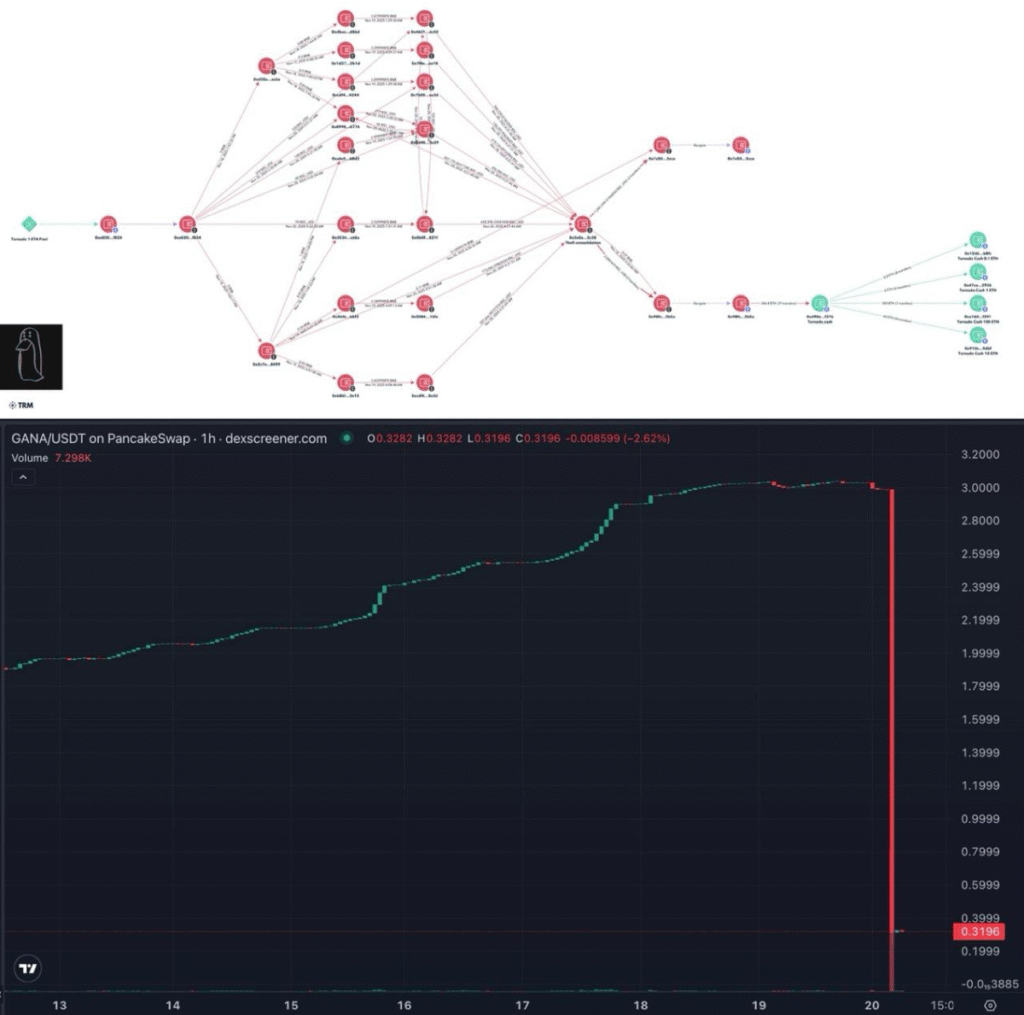
The GANA exploit marks another significant blow to security within decentralized finance, particularly affecting a project that aimed to create “next-generation payment infrastructure” in an effort to bridge traditional finance and Web3 ecosystems.
Read also: Masked Gang Steal Crypto Worth £1.1M & £450K Luxury Watch in Terrifying Car Kidnap
Cross-Chain Money Laundering Operation
Immediately after the GANA Payment exploit, the attacker began obscuring the trails of the stolen funds by routing 1,140 BNB (around $1.04 million at the time) through a Tornado Cash service on the BSC network. Then, via an interoperable bridge, the stolen assets were sent to Ethereum, where another 346.8 ETH (around $1.05 million) was sent through Ethereum’s Tornado Cash mixer.
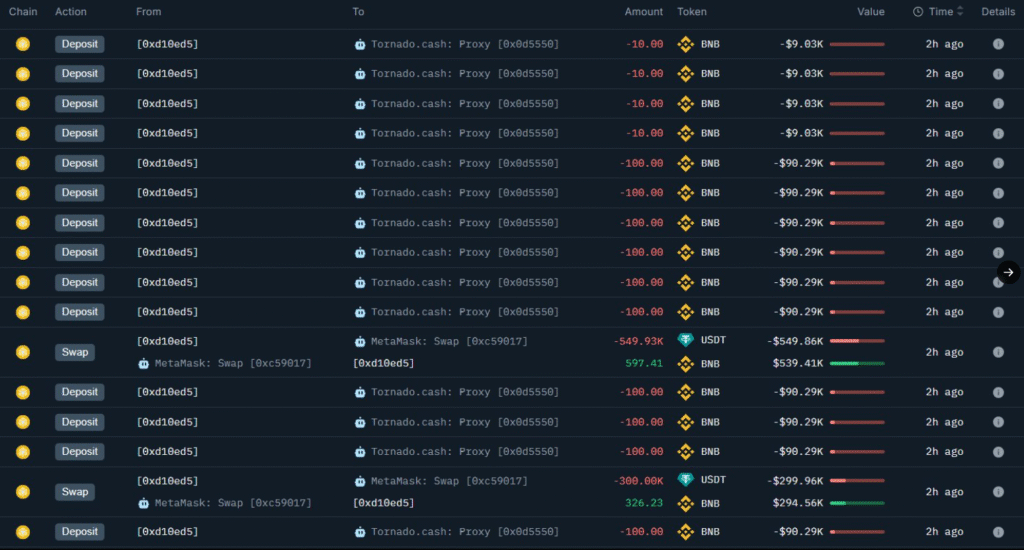
Blockchain forensic data shows the hacker still has control of 346 ETH ($1.046 million) sitting dormant at an Ethereum address. This may suggest either a calculated time delay in laundering or a potential plan for a future attempt to exploit another decentralized finance (DeFi) protocol.
Read also: Epstein Bitcoin Meetings Reveal Early Crypto Discussions with Bitcoin Core Dev & Powerful Figures
Project Future Uncertain After Major Security Failure
The GANA Payment Exploit leaves the project’s ambitious vision of “rebuilding global payment infrastructure” in serious jeopardy. Before the attack, the GANA project marketed itself as combining Web2 merchant integration with Web3 transparency, offering cross-border remittance and digital asset payment solutions.
The substantial financial damage from the GANA Exploit raises questions about the project’s security practices and whether it can regain user trust while addressing the fundamental vulnerabilities that enabled the multi-million-dollar breach.
FAQs
What was the GANA Payment Exploit?
The GANA Payment Exploit refers to a security breach on the Binance Smart Chain that resulted in over $3.1 million being stolen from the payment infrastructure project through unauthorized access to project funds.
How did the attacker launder money after the GANA Payment Exploit?
Following the GANA Payment Exploit, the attacker utilized Tornado Cash on both BSC and Ethereum networks to obscure transaction trails, bridging stolen funds between chains to complicate tracking and recovery efforts.
What is the current status of funds from the GANA Payment Exploit?
Following the GANA Payment Exploit, 346 ETH (around $1.046 million) remains in the attacker’s Ethereum wallet, while approximately $2.1 million has already been processed through privacy mixers, making recovery increasingly challenging.
For more crypto exploit stories, read: Critical WhatsApp 0-Click Vulnerability Exploited via DNG File – Watch Your Crypto!


